Are your IT systems already compromised?
The “cyber war” is raging! Various recent studies show frightening facts and figures.
This leads to the conclusion that, despite existing security and prevention mechanisms, there is obviously a very high probability that a company’s IT infrastructure will be compromised sooner or later – or has already been compromised. This risk can be attributed primarily to the following factors:
- Poor prevention
A lack of vulnerability management increases the potential attack surface. - Inadequate detection
Attacks and attempted attacks are not detected at all or are detected far too late.
Based on our expertise in the areas of pentesting, vulnerability detection, data analytics and security operations, we have developed a suitable solution: Trovent Managed Detection & Response (MDR).

Overview:
What is Trovent MDR?
The main aim of our MDR solution is to identify anomalies that indicate security-relevant incidents as quickly as possible.
With this effective attack detection, “digital intrusions” can be found at an early stage to prevent damage in the form of production downtime, data theft, blackmail and more.
Trovent MDR:
What does it offer in detail?
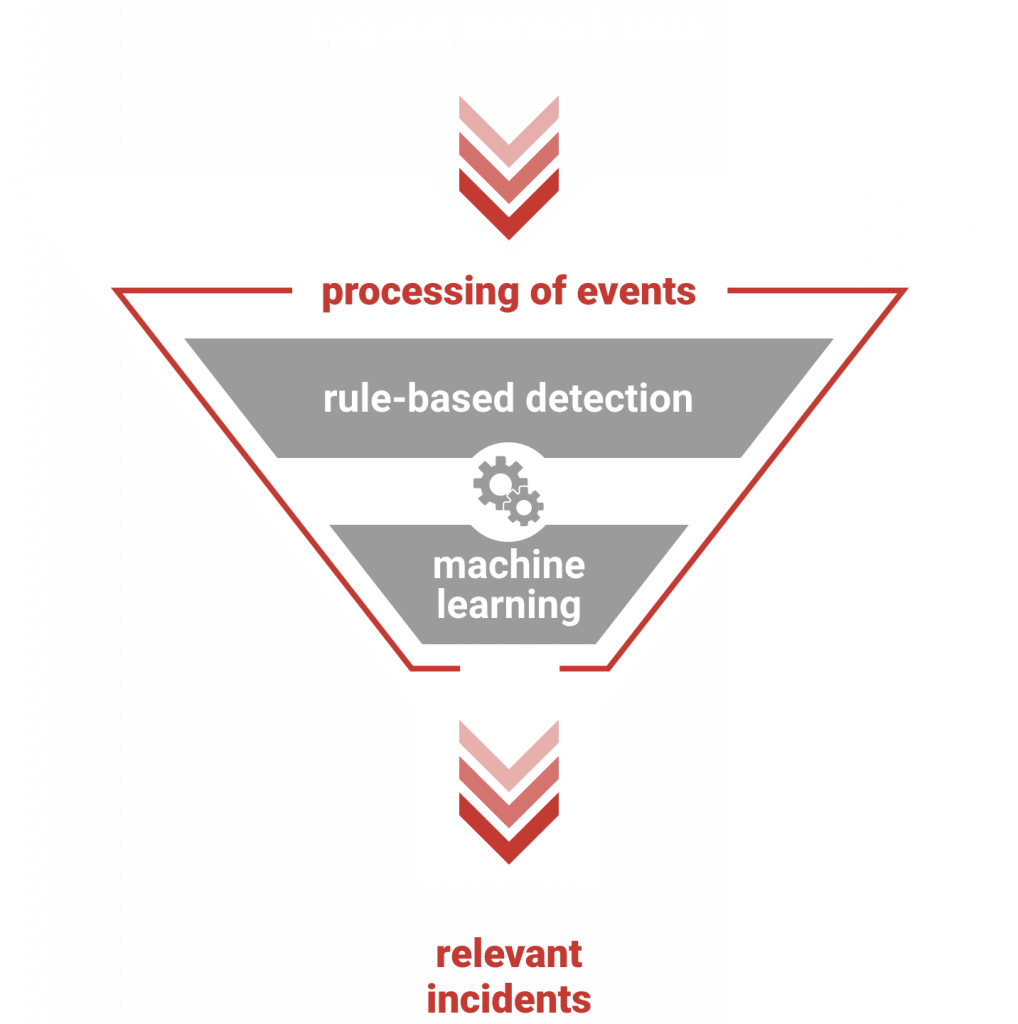
Trovent MDR can automatically detect security-relevant incidents from a flood of log data messages and network flows. To do this, we rely on rule-based processing and machine learning algorithms.
The result: Trovent MDR generates the lowest possible data volume with high information value from a high data volume with low information value.
Our MDR solution achieves this without interfering massively with existing IT infrastructure! Our attack detection solution only uses the data that your infrastructure already provides. It therefore works “agentless”, i.e. without repercussions.
Using existing knowledge effectively:
MITRE ATT&CK
Trovent relies on the MITRE ATT&CK framework, among others, as the basis for implementing the most effective detection of security-relevant incidents in order to ensure broad coverage of possible attack scenarios, methods and techniques.
In Trovent MDR, the ATT&CK knowledge base is used as the basis for the development and maintenance of rule-based and machine learning-supported attack/threat detection.
Why we use Machine Learning
Rule-based detection of potential attacks is a solid foundation. However, in the context of diverse and rapidly changing attack patterns, it is no longer sufficient. This is why Trovent also relies on Machine Learning in its MDR solution.
Machine Learning (ML) makes it possible to automatically detect unknown attack patterns. The algorithms used by Trovent MDR increase the detection rate of attacks and attempted attacks and at the same time significantly reduce the processing effort.
Use MDR as a service
Even the best attack detection is of no use to a company’s IT security situation if there are no processes and personnel capacities to respond promptly and appropriately to the security incidents detected. This is why we always deliver our attack detection solution as managed detection and therefore cyber security “as a service”.
We deliver detection and response – as an attack detection solution that can be flexibly adapted to the conditions of your existing IT infrastructure.
What we offer
Continuous tuning of detection rules and algorithms
The evaluation of potentially security-relevant messages
The exclusion of false positives (false alarms)
Detailed analysis of complex incidents
Concrete recommendations for action to contain the risk of damage
In short: We operate the system and manage the majority of the response process. This allows you to massively increase your detection and response capacity without our MDR flooding your existing IT department with a flood of alarms and reports from a wide variety of sources.
- Normalisation
- Pre-processing
- Rule-based
- Correlation
- Machine
learning
- Remove false positives
- Assess
relevance - Enrichment
- Verification of level-1 analysis
- Complex cases
- In-depth
analysis
- Reduce damage potential
- Minimise risk of contagion
- Implement
recommendations - Containment
Build up knowledge automatically
In order to maximize the possibilities of automated attack detection, the availability of knowledge about components and correlations in the existing IT infrastructure is of crucial importance.
For this reason, Trovent MDR uses the Trovent Context Engine, which is based on a graph database.
The Trovent Context Engine enables the automated creation of knowledge about infrastructural relationships in the monitored IT infrastructure. This significantly accelerates your security operations processes.
How will Trovent MDR be integrated?
The Trovent MDR system is able to process log data and network metadata (flows) from any source. Cloud, on-premise or hybrid – everything is possible.
This means that logs from Azure, M365, GCP (Google), AWS and a large number of common cloud applications are on board the Trovent MDR system in no time at all.
Logs from on-premise systems such as Windows Server, Linux Server, firewall/proxy, mail gateway, VPN gateways, antivirus solutions and routers/switches (netflow/sflow) can also be received.
And what is the required infrastructure for Trovent MDR itself? We can operate the MDR system on-premise or in your preferred cloud. Deployment takes place within minutes, regardless of your preferred target infrastructure.
How does your company benefit from Trovent MDR?
From the information security officer to the management: The biggest advantages of Trovent Managed Detection & Response from different perspectives.
- Insight into network traffic
… and the behavior of the IT infrastructure as a whole. This enables rapid detection of unwanted network traffic flows and compromised hosts. - Fast deployment
No lengthy implementation and tuning phase. The detection capabilities of the Trovent platform are based on the MITRE ATT&CK framework, which means that it is ready to use immediately after deployment and connection of the data sources. - No massive intervention
Trovent MDR is embedded in the existing IT infrastructure. The solution draws maximum benefit from existing data sources such as logs, network flows and events from third-party systems (e.g. host IDS or AV system) for the detection of security-relevant incidents. - Passive data sources
The data sources are largely received passively. Therefore, no invasive interventions in the existing IT infrastructure are required. - Acceleration through ML
The targeted use of Machine Learning algorithms enables the detection of correlations that human analysts cannot identify in a reasonable amount of time. In addition, these can be correlated with findings from rule-based detection. - Delivery as a service
Trovent MDR means that experienced experts take care of the topic. This means that the solution is ready to use immediately, without the lengthy and costly process of setting up a dedicated, internal security operations team. - Increased productivity
A flood of log and event data is avoided. The focus is on the really security-relevant events. - High flexibility
The use cases can be adapted to the environment as required at any time using a dedicated editor. The same applies to integration into existing security operations processes. - No cost explosion
… due to expensive license models based on the number of events per second or data volumes. Billing is based on volume-independent flat rates. - Transparency and traceability
No “black box” approach. The detection of security-relevant events is traceable at all times.
- Compromised or not?
Trovent MDR provides the technical basis for determining whether the integrity and confidentiality of your IT infrastructure has been or is being breached.
Objective assessment of the threat situation and the maturity level of the company’s cyber security infrastructure and processes. - Minimization of additional costs
Trovent MDR is offered as a service. This eliminates the lengthy and expensive process of setting up your own dedicated security operations team. - Increased resilience
Attacks and threats are detected immediately. This allows appropriate measures to be initiated immediately. This avoids lengthy, costly IT infrastructure outages. - Protection of “information crown jewels”
Confidential customer data, sensitive business information, intellectual property and the like are effectively protected. This actively prevents costly reputational damage. - No dependency
It is possible to work towards independent operation of the Trovent MDR solution.
- State of the art
The ‘state of the art’ required by Art. 32 GDPR is demonstrably used to “…ensure the confidentiality, integrity, availability and resilience of the systems […]”. - Immediate detection
Possible breaches of confidentiality and integrity can be detected at an early stage. This enables the data protection officer to immediately report possible incidents to the responsible authorities in accordance with Art. 33 GDPR. - Preparation for a crisis
A functioning anomaly detection system requires the central collection of network traffic/log data. In the event of a crisis, this in turn provides the data basis for recognizing when, to what extent and, if applicable, by whom data and infrastructure have been compromised.
Prevention of reputational damage due to loss of personal data or malicious use of this data by third parties. - GDPR-compliant processing
Personal content in the log data received (account names, IP addresses, email addresses, etc.) can be pseudonymized. If necessary, in the course of processing a security-relevant incident, the original values belonging to the respective pseudonym can be viewed in a separately protected storage area by appropriately authorized employees of the customer.
- Assessment of the initial situation
Thanks to Trovent MDR, objective statements can be made at any time about the risk to the IT infrastructure and information security. - Basis for risk analysis
A functioning risk assessment of information security in accordance with ISO 27001 or IEC 62443 and other standards requires that you proactively identify your weak points in order to be able to assess and quantify risks. - Assess and quantify risks
Trovent MDR creates the basis for this. - Compliance with standards and legal requirements
The use of Trovent MDR enables the implementation of the “state of the art” and the fulfillment of the obligation arising from the IT Security Act 2.0 to use systems for attack detection.
Test Trovent MDR in your environment

Would you like to see Trovent MDR in action in a real environment?
We would be happy to demonstrate the performance of our platform in your IT infrastructure. Get in touch with us!
We will arrange the framework conditions for the test use of our MDR security solution as quickly as possible.
Looking for detection expertise?
Do you see a need for action in your IT security architecture?
Would you like to implement improved attack detection in your
implement improved attack detection in your company?
Would you like to talk to an expert on the subject of cyber security?
We will be happy to provide you with a free consultation.
