Automatically build knowledge.
Accelerate security operations.
Working in the Security Operations Center can be tedious. Among other things, SOC analysts have to manually process countless events – including false positives – and compile missing information on infrastructural correlations. It is also necessary to assess which systems are exposed to a high risk.
Appropriate rules and algorithms can be used to identify potentially security-relevant incidents. However, an event is difficult to assess without knowledge of the interrelationships. As a result, critical situations are recognized too late or not at all.
This means that when considering events, the context in which they occur is crucial for their evaluation from a safety perspective! The Trovent Context Engine helps you with precisely this important task.

What is the Trovent Context Engine?
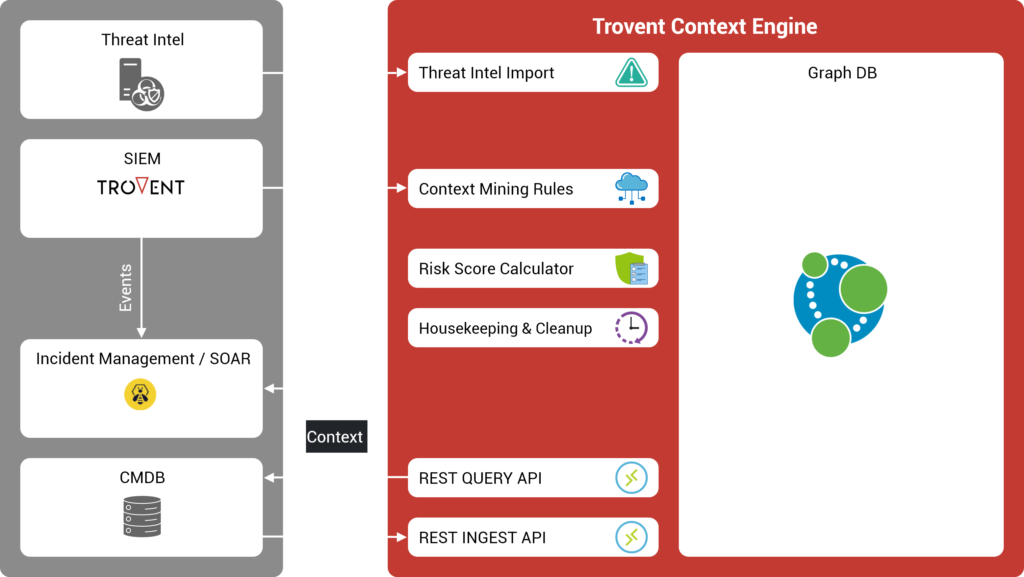
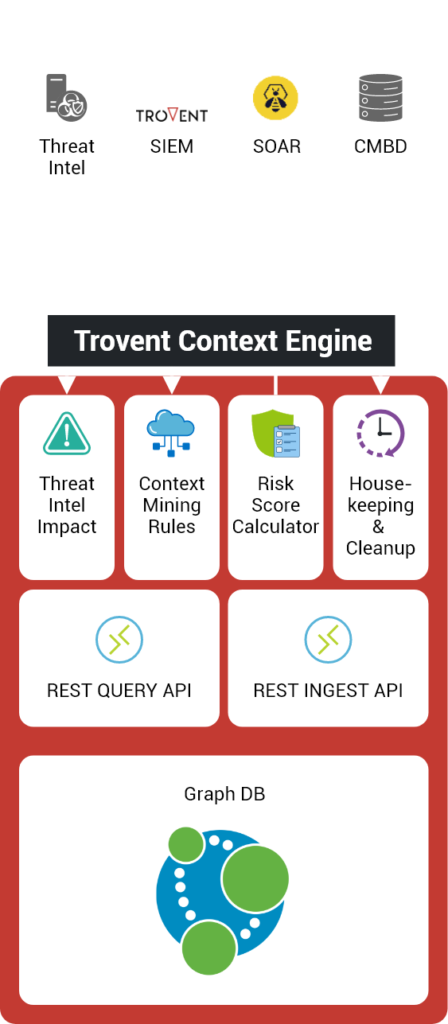
The Trovent Context Engine automatically builds context knowledge in the background – without the use of additional agents – by processing log data sources that are already available. The results are mapped in a high-performance graph database.
You can use the correlations built up there as a data source for
- Automated event/incident processing in SOAR platforms
- Downstream, automated analyses in SIEM/anomaly detection systems
- Detailed SOC analyses
What does the Trovent Context Engine offer?
The Trovent Context Engine automatically generates basic data and correlations, which in turn can be used for downstream machine analysis.
While a SIEM searches logs for attacks, the Context Engine searches specifically for information about the assets of the organization’s IT infrastructure. These include:
- Systems with their hostnames and IP addresses
- Users with their accounts
- Operating systems and their various versions
- Software packages with characteristic registry keys and files
More advantages
In addition, anomalies and attacks detected by a SIEM are stored in the context engine. Together with the underlying representation as a graph, this makes it possible to continuously calculate key risk figures for each asset.
Which assets are particularly exposed? Which are affected by attacks? These questions can be answered with the Trovent Context Engine.
How is it integrated into SOC operation?
The Trovent Context Engine can be seamlessly embedded into your existing SOC infrastructure without the installation and distribution of additional agents and without the implementation of complex integration or migration projects.
The solution is therefore “non-intrusive” and completely non-reactive to the existing IT infrastructure.
There are several ways in which you can use the Trovent Context Engine as an accelerator for efficiency, productivity and results in SOC operations:
As part of Trovent MDR
In this case, the connection of the Context Engine is particularly trivial, as it is an integral part of Trovent MDR – our Managed Detection and Response solution.
As a data enrichment source
The Trovent Context Engine serves as a source for an existing SIEM or SOAR platform in order to further increase the degree of automation of SOC playbooks. The processing time for individual incidents can be significantly reduced in this way. In this case, the Context Engine is addressed via the available REST QUERY API.
As a separate component
The Trovent Context Engine receives the infrastructure/application logs already collected by an existing SIEM. The aim is to use the automatically recognized correlations to detect security-relevant incidents that have not yet been noticed.
When does your SOC team need the Trovent Context Engine?
The following examples from SOC practice show why it is so important to know the interrelationships precisely.
Situation
The target of a potentially risky connection is not an employee’s regular PC, but the HR department’s database server. This contextual knowledge significantly influences the assessment of the severity of a detected attack or attempted attack.
Risk
If the logical connection between host, application and asset owner is not automatically available in the SOC at first glance, the initial analysis may result in a serious misjudgement of the risk.
Situation
An unknown person has been trying to guess the password of a user account for 20 minutes in order to access the private area of the public website. A classic brute force attack! However, this user account also exists on several internal systems.
The risk
If the intrusion attempt is successful, the attacker has a good chance of gaining access to internal data. However, a dedicated analysis of the daily, mostly automated brute force attacks is neither possible nor sensible in terms of personnel. Therefore, the criticality of the individual attacks resulting from the context must be recognized automatically so that the Security Operations Center can correctly classify the risk of the attack.
Situation
A new exploit becomes known. It is not immediately clear which internal systems have already been sufficiently patched. How can the systems that still need to be patched be identified without spending a lot of time? Which users need to be informed if the patch is to be applied at short notice during office hours?
The risk
If this knowledge is not automatically and immediately available to the Security Operations Center, a lot of time has to be invested in searching for and compiling basic information. This can mean valuable hours and days during which attackers can already use the new exploit to their advantage undisturbed.
An image of the normal state of the IT infrastructure, including its users and applications, is generated. From this, you can automatically recognize when the image of the infrastructure changes – for example due to an external attack.
Work processes in SOC operations are greatly accelerated as you receive the necessary contextual knowledge directly and immediately. This means that significantly less time is lost in manually gathering information and identifying false positives.
Use the automated calculation of the risk score for all hosts and users combined in the Context Engine! For example, you can better prioritize the security-relevant incidents as well as the medium and long-term improvement measures for your IT infrastructure.
The Trovent Context Engine increases the benefits of your SOC infrastructure without having to change the existing infrastructure.
How your SOC benefits from the Trovent Context Engine
Test our Context Engine

Are you interested in our Context Engine? Would you like to see it in action in a real environment?
We would be happy to demonstrate the performance of our technology in your IT or SOC infrastructure!
Get in touch with us and we will arrange
the framework conditions for the test deployment as quickly as possible.
We are happy to advise you
Do you see a need for action in your IT security architecture?
Would you like to implement improved attack detection in your
implement improved attack detection in your company?
Would you like to talk to an expert on the subject of cyber security?
We are at your disposal.