#testenfürdenwinter - 30% günstiger!
Wir reduzieren ab sofort die Preise unserer Penetrationstests und Schwachstellenanalysen um 30% für alle Unternehmen und Organisationen, die täglich unsere überlebenswichtige Infrastruktur in Deutschland am Leben halten.
Identify vulnerabilities before your adversary does
Penetration testing is an extremely important cyber security measure. But what exactly does your organisation need?
Our Pentest Configurator allows you to summarise your requirements and we’ll contact you with an initial proposal.
Would you like expert advice on the appropriate focus and target of a penetration test? Trovent offers free consultancy sessions to help you define the optimal scope for your specific penetration test requirements.
Prevention — less costly than disaster
The objective of a penetration test is the prevention of a deliberate or inadvertent cyber attack on an organisation’s IT infrastructure. Put simply, a penetration tester thinks and acts like a potential attacker in trying to identify vulnerabilities and ways of exploiting these.
Act proactively and take precautionary measures before your IT systems are compromised.
Successful attacks and resulting data breaches have far-reaching and costly consequences.
Professional hackers operate with well-crafted plans and capable tools. So does Trovent’s pentesting team!

Penetration testing:
What is it?
A penetration test has the core objective of specifically identifying vulnerabilities in targeted applications or IT infrastructure and to determine ways in which these might be exploited for the purpose of a malicious attack.
This can be achieved, for example, by gaining unauthorised access to other areas of the targeted IT infrastructure (lateral movement) or by increasing the privileges of a particular user account (privilege escalation).
Penetration testing process
Our penetration testers attack your IT infrastructure on your behalf – with the mindset and approach of a typical adversary.
The key to successful penetration testing: A clear, structured, repeatable and well-documented modus operandi that produces results of consistently high quality.
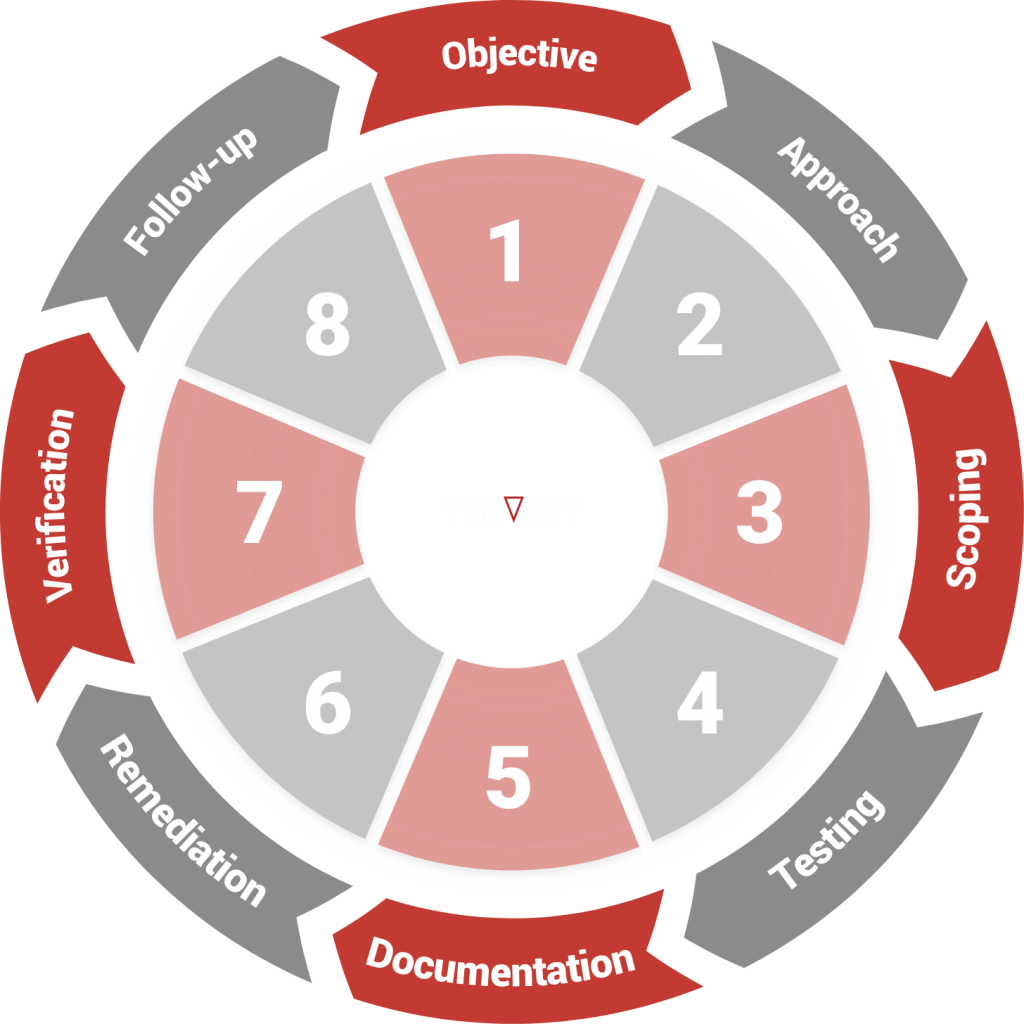
Relevant standards
- OWASP Web Security Testing Guide
The Open Web Application Security Project’s (OWASP) Web Security Testing Guide is a globally used standard. It describes detailed procedures for identifying vulnerabilities in web applications. - Penetration Testing Execution Standard
The Penetration Testing Execution Standard (PTES) was created in 2009. Since then, it has served as a recognised standard among experienced penetration testers for test execution. - Test classification – Federal Office for Information Security
In the run-up to penetration text execution, the informational basis and aggressiveness of the penetration test must be agreed between client and Trovent. For this purpose Trovent uses the penetration test classification provided by the German Federal Office of Information Security.
Focus and scope
- Pentesting focus
Which parts of your network infrastructure, which applications and which systems should be tested? - Location and time window
When and where should the penetration test take place – on site or remotely? - Informational basis
From white box to black box: What level of prior knowledge does the pentester have about the target system? - Aggressiveness
Should vulnerabilities only be identified or actively exploited? - Methods
Which techniques can be used as part of a penetration test?
Documentation and retesting

Results are recorded and documented as the penetration test progresses.
Detected and verified vulnerabilities are assessed in-depth and rated in accordance with the Common Vulnerability Scoring System (CVSS).
Vulnerabilities identified, corresponding evidence as well as recommended mitigation measures are described in detail.
Once remediation actions have been implemented, we retest target systems to verify that identified vulnerabilities have been addressed.
Key benefits of a penetration test
The current cyber security environment is characterised by a high-risk threat landscape and rapid pace of change. This challenging environment is compounded by a confusing and intransparent market of security products and solutions.
In this context, the prioritising cost effective improvement measures for your IT (security) infrastructure are a major challenge. A penetration test can provide valuable insight into critical weaknesses and therefore directly contributes to your ability to make prioritisation decisions with maximum improvement impact!
A penetration test shows you where there are large and small gaps in your IT infrastructure.
Based on the results, you are able to close identified vulnerabilities in a targeted manner. You reduce your risk of falling victim to accidental or targeted hacker attacks.
By closing critical gaps, you reduce the risk of a widespread failure of your IT infrastructure due to cyber attacks. And you protect your “information crown jewels” from theft.
You reduce your costs! Taking precautions for your cyber security is significantly cheaper than an emergency.
Our areas of focus
Why perform penetration tests?
A Trovent penetration test provides you with important insights into the status of your IT infrastructure and the IT security processes in your company. These findings can be used in a targeted manner to identify and prioritize further technical and organizational improvement measures.
For example, a pentest can lead to the realization that:
- The introduction of ongoing vulnerability management is necessary and sensible in order to ensure the prompt detection and elimination of vulnerabilities.
- The implementation of an attack detection solution (Managed Detection and Response) is necessary and sensible in order to be able to recognize attack activities at an early stage. Attacks or attempted attacks become visible before widespread damage occurs.
Pentesting by Trovent.
Our penetration testers have a wealth of experience from a range of industries:
- Insurance / financial services
- Healthcare / eHealth
- Automotive
- Critical infrastructure
- Consumer goods
- Application development
- IT service providers
- Manufacturing
And of course our pentesters are trained accordingly and have obtained highly respected certifications, including Offensive Security’s OSCP.

Crazy about security
In addition to the penetration tests we perform for our clients on a daily basis, we’re also actively hunting for vulnerabilities in our spare time. eHealth applications and the broad field of wearables have been of particular interest to our security research team. The reason is simple: These applications and devices handle very sensitive personal data. And unfortunately, they’re often far from secure – at least from what we’ve seen so far.
We’re happy to share our findings with our peers in the security research community and anyone else interested in cybersecurity. You’ll find details in our security advisories and blog posts.