Accelerate IT forensics with automation
The IT forensics plays a crucial role in responding to IT security incidents by analyzing potentially compromised systems and mitigating damage.
IT forensic experts have to overcome many challenges in their daily work:
High time pressure
Too little time to analyze all available data and processes
Hardly any automation
Analysis work is mostly done manually with many tools
False negatives
There is always a risk that something may be overlooked
Narrow time window
Long-term monitoring is often not possible
For these reasons, important findings can remain undiscovered. This is why we have developed the Trovent Forensic Appliance based on the many years of experience of IT forensic experts, to make forensic work much easier.

Overview: Trovent Forensic Appliance
Our IT forensics tool makes the following possible:
- It is immediately operational in moments of suspicion and in actual emergencies.
- It provides immediate insight into the communication relationships and behavior of a potentially compromised host.
- It reduces time-consuming analysis processes through automation.
- It significantly accelerates forensic workflows.
Trovent Forensic Appliance:
Transparency, acceleration and automation
These are the advantages that IT forensic experts benefit from when using the Forensic Appliance:
- The Trovent Forensic Appliance is integrated “inline”. It allows granular monitoring of all network communication connections and connection attempts of (potentially) compromised hosts.
- It works as a firewall to completely or selectively disconnect the potentially compromised host from the network. Connection attempts to the public Internet can be completely blocked or selectively allowed in order to observe the behavior of the host step by step.
- It allows granular monitoring and evaluation of all DNS queries. This makes it possible to determine whether attempts are being made to access malicious URLs.
- Our IT forensics tool provides a honeypot based on OpenCanary to monitor the behavior of (potentially compromised) hosts. The honeypot is of course isolated from the rest of the company network.
- There is a range of emulated services to secure infected systems in a “hybrid sandbox”. The controlled accessibility of the real infrastructure minimizes the risk of unintentionally alerting the attacker(s).
- It is possible to protect the non-compromised part of the network by completely controlling the network traffic.
The communication behavior of a probably compromised host can be automatically compared with a reference system, for example with the workstation image of a standard user. - Security-relevant deviations in behavior are detected – without time-consuming manual effort.
How it works: How is the Forensic Appliance structured?
- The Trovent Forensic Appliance is a single device that is connected to the company network. The hardware used has a second network connection, which is connected to the system to be analyzed. From now on, the Trovent Forensic Appliance controls the data traffic as a firewall.
- The system being forensically analyzed remains in the network. However, it is isolated from the network and cannot cause any damage.
- If the logs from other devices in the network are sent to the Trovent Forensic Appliance, a decision can be made on the basis of the behavior as to what the system to be analyzed may and may not do.
- Alternatively, it is possible to connect a reference system (e.g. standard workstation) in parallel to the system under investigation in order to use its behavior as a baseline and detect deviations in the behavior of the system under investigation.
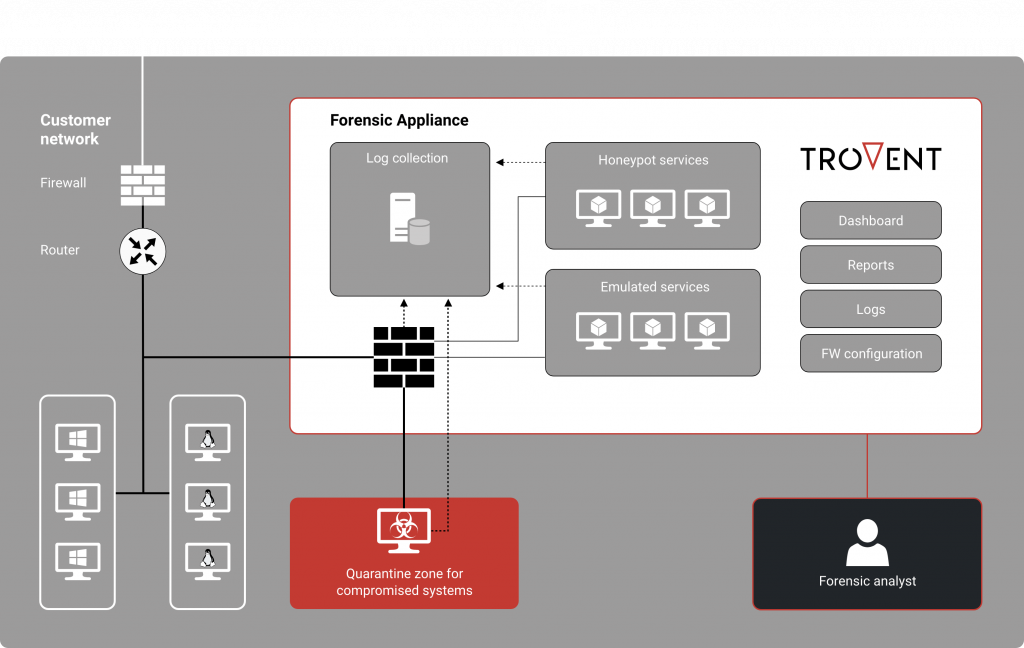
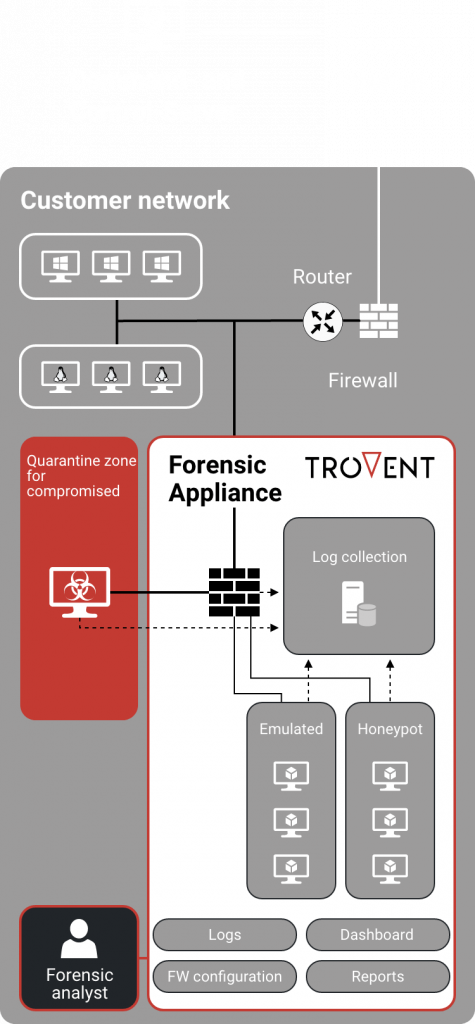
The use of emulated services enables a further control option. The outgoing traffic of the potentially compromised system can be selectively and transparently redirected to these services. This means that the system being forensically examined does not access actual targets, but emulated services. These are available for certain protocols, for example HTTP and SMTP. The Trovent Forensic Appliance logs all processes granularly.
Furthermore, integrated honeypot services make it possible to observe reconnaissance and lateral movement attempts by one or more attackers – without having to allow real access to the company network.
Comprehensive overview
The Trovent Forensic Appliance:
- a comprehensive view of all logs,
- and control over the connections that are allowed, blocked and redirected to emulated services,
so that the actions of the system to be analyzed are always visible.
Scenario of use
Our customers use Trovent Forensic Appliance most frequently for the following applications.
Systems behave conspicuously for a short time, but do not show any permanent and obvious symptoms of compromise.
Unwanted (communication) behavior that deviates from set configuration standards can be detected in one or more systems.
There is an actual compromise. However, the analysis of the ongoing attack cannot take place in the laboratory because the attacker(s) would recognize this (keyword: “sandbox evasion”). In addition, the IT forensics investigation must not take place in an unprotected network.
Network communication, process and user data is automatically collected and visualized. Integrated honeypot services are also available for in-depth behavioral analysis of the compromised device. From the IT forensic specialist’s point of view, this saves a significant amount of manual work.
Network connections are successively released based on the automatic comparison with reference systems. This allows the behavior of the compromised system to be observed step by step. It is also possible to automatically interrupt network connections when a defined kill chain phase is reached.
Using the Trovent Forensic Appliance as a sensor enables patient observation of a potentially compromised host, thereby reducing the risk of false negatives. There is less need to frantically search for symptoms in a limited amount of time – symptoms that may only be observed at longer intervals.
Based on the technology already used for the Forensic Appliance, a company-wide solution for attack detection (Managed Detection and Response) can be set up seamlessly.
Advantages for forensic work
Das sind die größten Vorteile der Trovent Forensic Appliance, von der IT-Forensiker und Computer Emergency Response Teams (CERT) profitieren.
Interested in the Trovent Forensic Appliance?

Are you interested in the Trovent Forensic Appliance? Would you like to see the solution in use in a real environment?
We would be happy to demonstrate the performance of our solution in your environment.
Please contact us! We will arrange the framework conditions for the test deployment as quickly as possible.
We will gladly advise you
Are you interested in automating parts of your forensic work? Do you have detailed questions about the functional possibilities of the Forensic Appliance?
Would you like to talk to an expert?
We will be happy to provide you with a free consultation.