How can the requirements of ISO 27001 be met with regard to technical vulnerabilities? We answer the most important questions. And we provide specific recommendations on how you can implement the requirements of the standard in practice.
Importance of ISO 27001
DIN ISO/IEC 27001, or simply ISO 27001 for short, defines the requirements that an ISMS (Information Security Management System) must fulfill. ISO 27001:2013 was valid for many years; the standard was slightly adapted in 2017. ISO 27001:2022 is currently valid.
An ISMS consists of procedures and rules within an organization that serve to permanently
- to define,
- control it,
- control it,
- maintain and
- continuously improve it.
In particular, the ISMS is used for the information security risk assessment required by ISO 27001. The risk assessment process must:
- Evaluate risks in terms of compromising the confidentiality, integrity and availability of information
- Identify risk owners
- Estimate and quantify the consequences of the occurrence of the respective risk
- Determine the probability of occurrence
- Prioritize risks according to their potential consequences and probability of occurrence
- Include clear criteria for risk acceptance
ISO 27001 focuses on technical vulnerabilities
In order to meet the requirements of ISO 27001, you must record and evaluate technical vulnerabilities in the information security risk assessment.
The normative Annex A of ISO/IEC 27001 explicitly addresses the handling of technical vulnerabilities in section 12.6.
Annex A of ISO 27001 states under A.12.6 that you must prevent the exploitation of technical vulnerabilities. Control A.12.6.1 (“Handling of technical vulnerabilities”) states:
“Information on technical vulnerabilities of information systems in use is obtained in a timely manner, the exposure of the organization to such vulnerabilities is assessed and appropriate action is taken to address the associated risk.”
This measure required in the normative Annex A of ISO 27001 for dealing with technical vulnerabilities can only be fulfilled through a consistently implemented vulnerability management process. This requires a suitable technical infrastructure and the corresponding expertise of the users.
Indeterminable risk = highest possible risk!
From numerous discussions with information security and IT managers, we know that most German companies do not currently have a functioning (ongoing!) process for dealing with technical vulnerabilities. This also includes many companies that have already implemented a certified ISMS in their organization.
In preparation for ISMS certification, companies often carry out a vulnerability check by means of a one-off vulnerability scan or penetration test. However, a one-off scan only has a very limited half-life!
It’s like a one-off system scan for viruses or malware: the results gradually lose their information value and validity with each passing day, as the scanned systems and the IT infrastructure as a whole change. At the same time, the threat also changes due to the emergence of new vulnerabilities and attack methods.
Recurring checks are therefore urgently needed. However, only very few IT managers carry out or commission these. This means that many companies are flying blind when it comes to their information security risk!
An information security risk assessment without
- knowledge of the technical vulnerabilities,
- the analysis of network traffic and log data,
- and an in-depth review of the IT systems
does not allow a realistic risk assessment – neither of the probability of occurrence nor of the damage potential.
As a result, the risk to IT security and therefore to information security cannot be determined. As a consequence, the highest possible risk for the respective company must be assumed.
Catalog of measures: How a process according to the ISO 27001 standard works
In order to meet the requirements of the normative Annex A of ISO 27001, a vulnerability management process is essential.
As in many other process-oriented management systems, the well-known principle of the PDCA cycle (Plan-Do-Check-Act) is also used in vulnerability management. The vulnerability management process is implemented as follows:
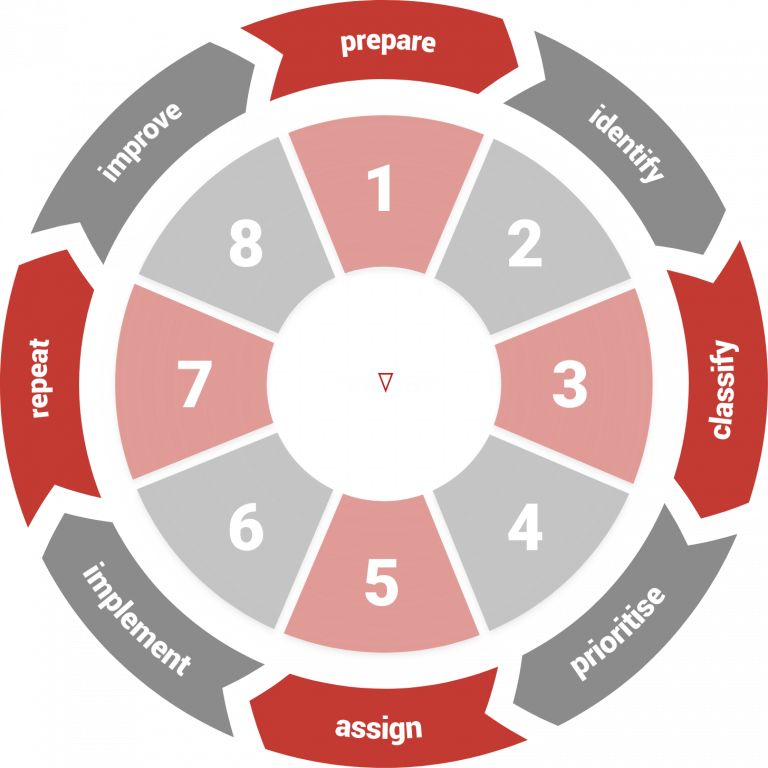
In the following paragraphs, we break down the process into its individual parts. We look at the process steps required to meet the requirements of ISO 27001 for the detection and elimination of technical vulnerabilities.
Step 1: Data collection and scan preparation
First of all, you need to determine which IT assets are available and which specific properties should be taken into account when checking for vulnerabilities. You can obtain the necessary data from the ISMS and the asset management system. This is primarily technical data such as IP addresses, network infrastructure and operating system information. You use this data to compile the correct parameters for the scan and prepare the scan configuration.
Do you not have the asset information available? Then you will need to conduct an initial survey – for example, a discovery scan – to gain an overview of the IT assets in your IT infrastructure.
Step 2: Perform scan and identify vulnerabilities
You carry out the scan using the previously created scan configuration. The scan usually results in a long list of technical vulnerabilities that are assigned to the respective IT asset that has been checked. You make the relevant information available to the ISMS via system interfaces.
Experience has shown that a scan very often reveals components or IT systems that were not previously recorded in asset management. You transfer the information collected via the scans (e.g. IP addresses, operating systems, etc.) to the asset management system.
Step 3: Evaluation of the results
The Common Vulnerability Scoring System (CVSS) is first used to assess the vulnerabilities. This metric takes into account various characteristics of a vulnerability. These include, among other things
- Attack vector: what type of access does an attacker need to exploit the vulnerability?
- Attack complexity: How complex is the exploitation of the vulnerability for an attacker?
- Authentication: Does the attacker first need to gain user rights in order to exploit the vulnerability?
However, the CVSS score alone is not enough to assess the significance of the vulnerabilities! Even a technical vulnerability that is considered serious can be harmless in a company-specific context. And a supposedly harmless vulnerability may lead to the failure of large parts of your infrastructure.
It is therefore important that you carry out a valid assessment. You must assess what impact the successful exploitation of a vulnerability will have on
- confidentiality,
- integrity
- and availability
of your company’s IT infrastructure and information assets. You must evaluate the potential impact in the context of your company’s circumstances – in particular the existing business processes.
Does your company already have an ISMS in place? If so, there is already documentation in which the importance of individual IT systems and information assets has been recorded.
Step 4: Prioritization
Once you have assessed the weak points, you must prioritize the implementation of improvement measures.
The key questions to ask yourself are:
- Which vulnerabilities have the greatest potential for damage if successfully exploited by a potential attacker?
- What is the probability that each vulnerability will be successfully exploited?
When prioritizing the measures, you should also determine how big the hurdles are to successfully close a vulnerability. Here are three examples:
- Is it a vulnerability that can be closed by simply installing a software patch that is already available?
- Does a procurement request for an industrial firewall need to be submitted because certain production systems need to be isolated from the rest of the IT infrastructure?
- Is a new purchase necessary because the system at risk cannot be properly protected and therefore poses a risk to the rest of the IT infrastructure?
The result of the prioritization process is a plan that takes into account the improvement measures to be implemented and the available resources.
Step 5: Assignment
The requirements of the ISO/IEC 27001 standard demand clear risk owners. Accordingly, you must assign an already identified, assessed and prioritized vulnerability to a responsible person. This enables them to implement the defined improvement measures.
Ideally, you should already have a change/incident management system in place. This allows you to easily assign the risk and the catalog of measures (“tickets”) instead of working with error-prone Excel lists.
Step 6: Improve and remedy
The risk owner must ensure that the recommended improvement measures are implemented to eliminate or mitigate the vulnerabilities assigned to them. He documents the implemented measures in the change/incident management system and adds the necessary asset information to the ISMS – for example, the applicable patch level.
Step 7: Follow up / verify / repeat
At the end of the process chain, you must track and verify whether the person responsible has actually implemented the improvement measures. This also includes the technical review.
Only after another successful test has been carried out do you mark the weak points in the change/incident management system as rectified. The vulnerability management process then starts all over again in line with the Plan-Do-Check-Act principle.

Why is a recurring process so important? You must carry out the cycle continuously in accordance with ISO 27001. Because, as already mentioned, you are constantly faced with these challenges:
- The “vulnerability landscape” is constantly changing.
- Attackers quickly develop exploits for new vulnerabilities.
- Your company’s IT infrastructure is constantly changing.
Therefore, the requirements of the normative Annex A of ISO 27001 can only be effectively fulfilled by means of cyclical vulnerability management and the associated improvement measures.
In summary, this means:
- You must obtain information about technical vulnerabilities in good time.
- You must carry out an assessment of each vulnerability.
- Take into account the actual risk to your organization from the vulnerability in question.
- Take appropriate, individual improvement measures or a comprehensive catalog of measures to reduce the risk to your company in a targeted manner.
How you can securely implement the high requirements of ISO 27001
Only with a mature process for vulnerability management will your company be able to significantly minimize the various threats and meet the requirements of ISO 27001.
However, implementing an effective process is easier said than done! If your company wants to establish a vulnerability management process or improve an existing, rudimentary process, it usually faces three main challenges:
- Lack of technical infrastructure: you don’t have the appropriate systems in place to target vulnerabilities.
- Lack of personnel capacity: They do not have enough internal experts to oversee the entire process.
- Limited experience: Those responsible lack experience in the introduction of suitable vulnerability management processes
What is the solution to prevent long start-up phases and delays in the introduction of an effective vulnerability management process? You can hire specialized service providers to get you up and running immediately.
Trovent: Your partner for vulnerability management
Our team provides the necessary complete package as a service. We have the right solution to meet the high requirements of ISO 27001 for technical vulnerabilities – from detection to assessment and elimination.
The Trovent service package includes
- The technical infrastructure to detect vulnerabilities.
- The personnel capacity to carry out the scans and to assess, prioritize, track and verify the identified vulnerabilities.
We attach great importance to ensuring that our service can be seamlessly integrated into your existing business processes. In this way, the introduction and improvement of a vulnerability management process can be carried out smoothly. In this context, our experienced consultants are of course also available to optimize your IT security processes.
Know your attack surface. Reduce risk.
In conclusion, it can be said: Only those who know their potential attack surface, analyze it continuously and actively evaluate and eliminate identified vulnerabilities are able to meet the requirements of ISO 27001 and the universally required state of the art techniques.