This deep dive reveals how a tool we developed in-house inconspicuously duplicates Windows tokens, bypasses antivirus signatures, and opens SYSTEM privileges.
The Evolution of Windows Privilege Escalation in the Age of EDR
In the ever-evolving landscape of offensive security, penetration testers and red teams face an increasingly sophisticated array of defensive measures. Traditional tools that once reliably escalated privileges on Windows systems are now quickly detected and terminated by modern endpoint detection and response solutions (EDR).
This post explores an advanced approach to Windows token manipulation that flies under the radar of contemporary security solutions.
The Problem: When Traditional Tools Fail
Meterpreter’s Incognito Module: A Burned Bridge
Anyone familiar with post-exploitation on Windows systems knows the Incognito module for Meterpreter. For years, it has been the go-to solution for stealing Windows access tokens and escalating privileges. However, its widespread use has made it a prime target for antivirus vendors.
Today, its fingerprint is so well-known that virtually every modern antivirus solution can identify and terminate it immediately.
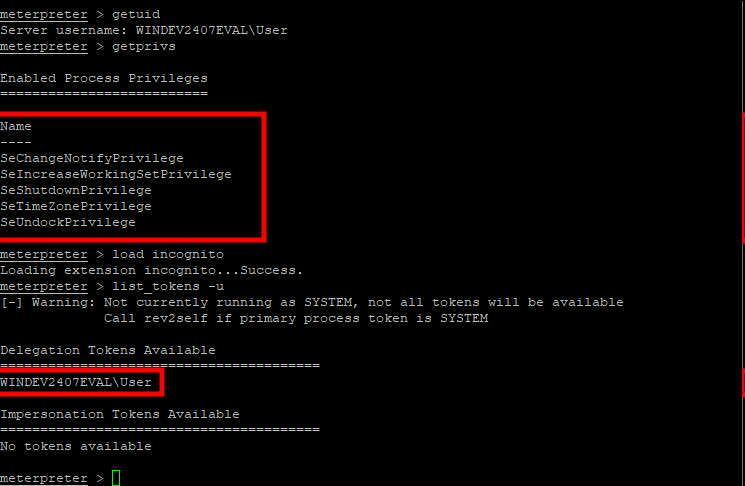 The initial token enumeration showing limited access without elevated privileges
The initial token enumeration showing limited access without elevated privileges
PsExec: Not So Stealthy Anymore
When working with a Remote Desktop Protocol session (RDP), security professionals often turn to Microsoft’s own PsExec tool from the Sysinternals suite.
While PsExec appears more legitimate than hacking tools, modern antivirus solutions have learned to recognize its abuse patterns. Many organizations now block PsExec entirely, preventing even legitimate administrative use.
Understanding the Stakes: Why SYSTEM Tokens Matter
Before diving into the solution, it’s crucial to understand why obtaining a SYSTEM token is essential, even when you already have administrative access.
The distinction between an administrator account and SYSTEM privileges can mean the difference between partial and complete system compromise.
The Privilege Gap
Even with administrative privileges and the SeImpersonatePrivilege enabled, certain critical operations remain off-limits. The most notable example is accessing the Local Security Authority Subsystem Service (LSASS) process, which runs exclusively in the SYSTEM context.
 The token enumeration reveals NT AUTHORITY\\SYSTEM when proper privileges are available
The token enumeration reveals NT AUTHORITY\\SYSTEM when proper privileges are available
The LSASS Barrier
Without SYSTEM privileges, tools like Mimikatz cannot dump credentials from memory, as they cannot access the LSASS process. This limitation significantly hampers post-exploitation activities and lateral movement capabilities.
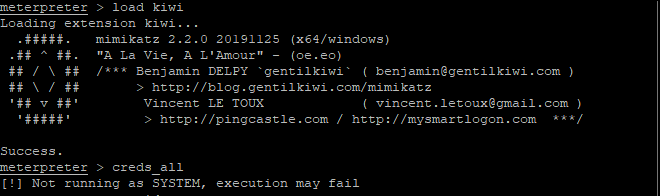 Mimikatz fails to dump credentials without SYSTEM-level access
Mimikatz fails to dump credentials without SYSTEM-level access
Only after successfully impersonating a SYSTEM token can an attacker gain full access to the system’s credential store:
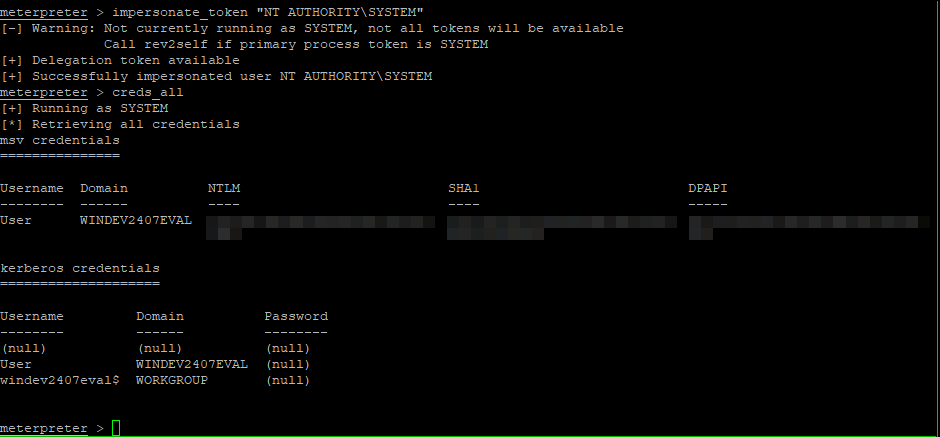 Successful credential extraction after obtaining SYSTEM privileges
Successful credential extraction after obtaining SYSTEM privileges
It is also possible to impersonate the SYSTEM token with the PsExec tool.
 Traditional PsExec approach – effective but easily detected
Traditional PsExec approach – effective but easily detected
Introducing tWATa: A Stealthy Alternative
To address the detection challenges posed by traditional tools, we developed the Trovent Windows Access Token Abuser (tWATa). This an open-source tool that performs the same token manipulation operations as Incognito and PsExec – while evading modern antivirus detection.
The Technical Foundation
tWATa leverages native Windows API calls to enumerate and manipulate access tokens without triggering security alerts. The tool employs a carefully crafted sequence of Win32 API operations that appear benign to security software while achieving powerful privilege escalation capabilities.
Token Enumeration Process
The enumeration phase uses the following Win32 API calls:
OpenProcess with the PROCESS_QUERY_LIMITED_INFORMATION flag
OpenProcessToken with TOKEN_QUERY and TOKEN_DUPLICATE flags
These calls allow tWATa to gather comprehensive information about each token:
User Information
Token Statistics
Integrity Level
Elevation Type
Token Manipulation Technique
The privilege escalation phase employs:
DuplicateTokenEx with TOKEN_ALL_ACCESS flag
SetThreadToken for token assignment
CreateProcessWithTokenW for spawning privileged processes
This combination allows tWATa to duplicate and impersonate any accessible token on the system without raising suspicion.
Practical Application: tWATa in Action
Interactive Session Usage
Using tWATa in an interactive session is straightforward:
Execute the tool to enumerate all available tokens based on your current privilege level
Identify the target token (typically from a SYSTEM process)
Enter the Process ID (PID) to impersonate the desired token
 tWATa displays all accessible tokens with detailed information
tWATa displays all accessible tokens with detailed information
 Successfully spawning a SYSTEM-level command prompt
Successfully spawning a SYSTEM-level command prompt
Remote Shell Integration
tWATa seamlessly integrates with reverse shell environments, providing the same functionality as the Incognito module without the detection risk:
 Token enumeration within a Meterpreter session
Token enumeration within a Meterpreter session
 Selecting and impersonating a SYSTEM token via command line
Selecting and impersonating a SYSTEM token via command line
 Successful migration to SYSTEM context within Meterpreter
Successful migration to SYSTEM context within Meterpreter
Defense Considerations and Ethical Use
While tWATa demonstrates the limitations of signature-based detection, it’s essential to understand this tool’s proper context:
Legitimate Use Cases
Detection Strategies
Organizations should implement:
Token access auditing (Event ID 4648, 4624)
Process creation monitoring with SYSTEM context alerts
Behavioral analysis beyond signature detection
Privileged access management (PAM) solutions
Technical Deep Dive: Understanding the Win32 API Abuse Chain
For security researchers and developers interested in the technical implementation, tWATa’s approach provides valuable insights into Windows security architecture.
The Token Lifecycle
Discovery Phase: Enumerate all running processes and their associated tokens
Selection Phase: Identify high-privilege tokens suitable for impersonation
Duplication Phase: Create a duplicate token with full access rights
Impersonation Phase: Apply the token to the current thread or spawn a new process
Execution Phase: Perform privileged operations under the new security context
This lifecycle exploits the legitimate token impersonation functionality built into Windows, originally designed for service accounts and system components.
Conclusion: The Ongoing Arms Race
As defenders, understanding these techniques is crucial for:
Developing more robust detection strategies
Implementing proper privilege separation
Creating effective incident response procedures
Training security teams on modern attack techniques
For offensive security professionals, tWATa provides a reliable tool for authorized testing while highlighting the importance of continuous innovation in security testing methodologies.
The cat-and-mouse game between attackers and defenders continues to evolve. Tools like tWATa remind us that security is not a destination but an ongoing journey requiring constant vigilance, adaptation, and understanding of both offensive and defensive techniques.
Resources and Further Reading
tWATa on GitHub – Official repository and documentation
Windows Token Manipulation Documentation – Microsoft’s official documentation
Meterpreter Incognito Module – Traditional token manipulation implementation
Sysinternals PsExec – Microsoft’s administrative tool suite
Remember: Always ensure you have explicit authorization before testing these techniques in any environment. Unauthorized access to computer systems is illegal and unethical.and
Are you looking for a Managed Detection & Response solution? Or would you like to learn more about how Trovent’s Context Engine works? Contact us! We’d be happy to discuss your needs and provide a demonstration of our solutions.
Sergey Makarov has been part of the Trovent team since 2020. As a Senior Security Specialist and Penetration Tester, he ensures secure IT environments for our customers. As a certified Red Team Operator/Lead, he knows exactly how cyberattacks work and how companies can protect themselves against them. Sergey is also an enthusiastic software developer. The tools he has developed – including YAETWi, tRWXi, tWATa, and tKMD – are available as open source projects on GitHub.